Integrating the Helix ALM License Server with identity providers
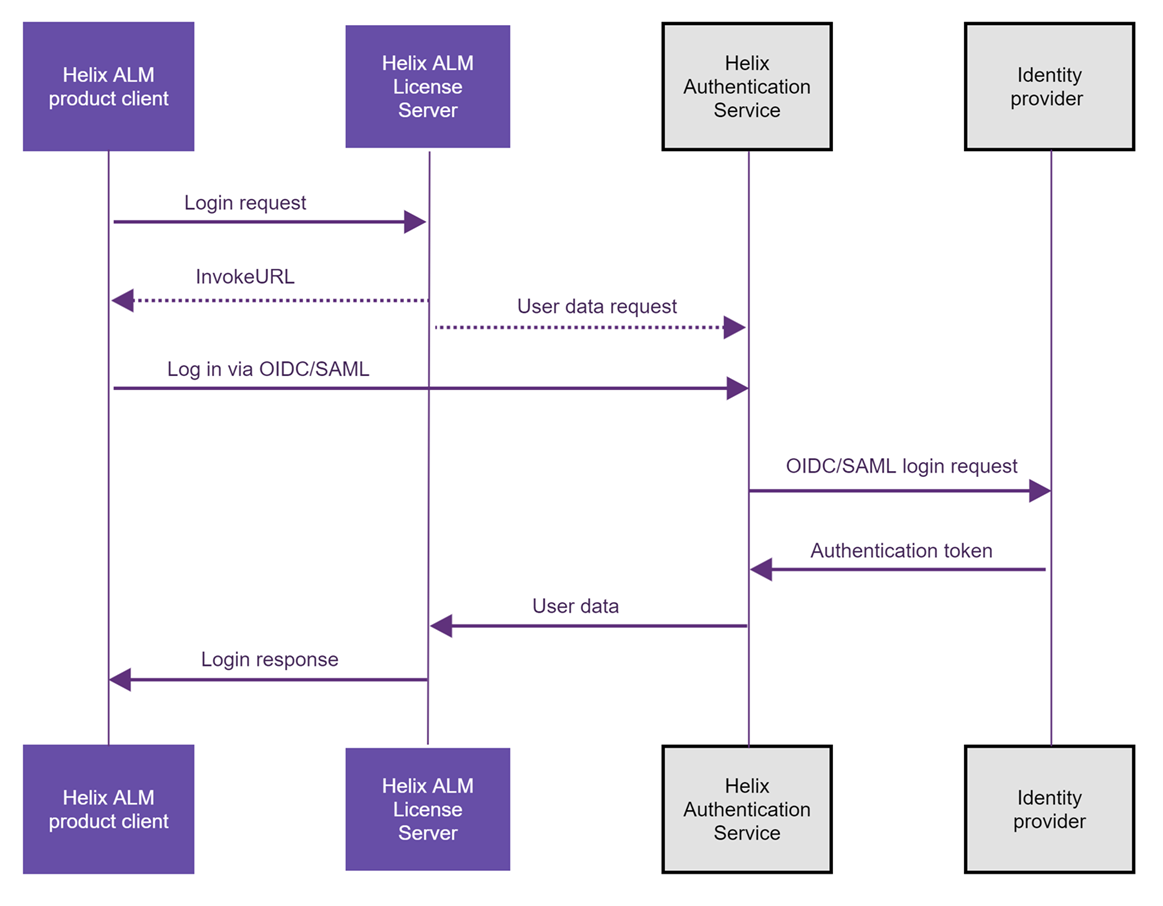
If your organization uses an identity provider that supports SAML or OpenID Connect authentication methods, such as Okta, you can configure the license server to use the provider for authenticating to Helix ALM, Surround SCM, and license server clients. This requires using the Helix Authentication Service (HAS), which lets you integrate various Perforce products with your identify provider.
If a user is configured to log in using a provider, they enter their Helix ALM product username on the product login dialog box or page and then the identity provider site opens in a browser. The user authenticates with the provider. If authentication is successful, they return to the Helix ALM product and can start working. Any user fields mapped between the license server and provider are updated with the field value from the provider in the user record on the license server.
Configuring identity provider authentication
To configure authentication with an identity provider:
1. An experienced security administrator needs to install and configure HAS. See Installing the Helix Authentication Service.
2. In the license server admin utility, enable authentication for OpenID Connect and SAML. See Setting authentication options.
3. Add a provider. See Adding OpenID Connect and SAML providers.
4. Add users to the license server if they do not already exist. See Adding users.
5. Select the provider for users who will use it to log in. See Setting authentication methods and passwords for users.
The following clients support authentication using an identity provider.
Helix ALM
Must use Helix ALM 2019.4 or later.
- Client (desktop and web)
- Server admin utility (desktop and web)
- Microsoft Outlook add-in
- Microsoft Visual Studio add-in
- Surround SCM desktop client integration
Helix ALM License Server
- Admin utility (desktop and web)
Surround SCM
Must use Surround SCM 2019.2 or later.
- Desktop client
- CLI
- Microsoft Visual Studio integrations — VSIP and MSSCCI
- Web application
Unsupported clients
The following clients do not support authentication using an identity provider.
Helix ALM
- REST API
- SOAP SDK
Helix ALM Data Warehouse
- Web application
Helix ALM License Server
- API
Surround SCM
- Analyze utility
- API