Manage permissions
To learn how to manage permissions, watch this video or review the instructions following the video.
View permissions
The Permissions tab displays tabs under it for Users, Groups, and Depot Tree.
To display the files and folders to which a user has access, click the user on the Users tab.
To display the files and folders to which users in a group have access, click the group on the Groups tab.
To display the groups and users that have access to a file or folder, click the file or folder on the Depot Tree tab.
To see which lines of the protections table control access to a user, group, or area of the depot, click the user, group or folder. The corresponding line in the protections table is highlighted. (If a user or group is neither granted nor denied access to a path by means of any entries in the protections table, the depot path displays "no access" and the "granted to" field is blank.)
To filter out lines in the right-hand pane, use the Access Level sliders to set the lowest and highest levels. The areas of the depot associated with the highlighted range of access values are displayed. To learn more, see Access level filter .
To see only those permissions that apply to a user’s workstation,
enter the IP address of the workstation in the Host IP filter
field. For example, permissions lines with a host value of
92.168.*.* and 192.168.1.* both apply to a
workstation at 192.168.1.10. To learn more, see Host IP filter.
To show files in the Depot Tree, click Show files.
Access level filter
The Access level filter allows administrators to view user permissions by filtering the depot view based on specific access levels. This filter enables you to select from various permission levels.

When you select an access level from the filter, the depot view updates to show only the rows that have that access level or higher. For example, if you select Read, the depot view displays all entries where the user has Read, Open, Write, Admin, or Super permissions. However, lower permissions, such as List, is not displayed.
Host IP filter
The Host IP filter allows administrators to view user permissions by filtering the depot view based on which host IP address a user is logging in from. This filter directly corresponds to the "Host" column in the protections table.
When you select asterisk (*) option in the Host IP filter, it will only match the lines that have '*' in the "Host" column of the protections table.
For example, consider the below protections table:
|
Access level |
User/Group |
Name |
Host |
Folder/File |
|---|---|---|---|---|
|
open |
user |
jackdev |
* |
//foo/... |
|
write |
user |
jackdev |
10.5.10.5 |
//bar/... |
When user jackdev logs in from a computer with IP address 10.5.10.5, he has access to the depots //foo/... and //bar/.... However, if jackdev logs in from a different computer with IP address 10.5.10.7, he will only be able to see the depot //foo/... and not any of the depots specified with a host IP. This is because access to //bar/... is restricted to when he logs in from 10.5.10.5.
When you select a specific host IP address from the Host IP filter drop-down menu, the depot view only displays the access levels and restrictions that are relevant when the user is logged in from that particular host. For example, if a user has "list access" from a specific host IP address, the depot view shows all entries in which the "Host" column includes that specific IP address. This indicates that the user has "list access" from that particular host IP address.
Edit the protections table
The protections table is displayed in the bottom pane of the screen. It
is a representation of the table used by the p4
protect command, with exclusionary lines shown in red. For more information on the p4
protect command, see p4 protect in the P4 CLI Reference.
To edit the protections table, use the built-in editor or click ![]() to edit the
protections table as text.
to edit the
protections table as text.
To deny access to a specific portion of the depot to a user or group,
use an exclusionary mapping. Place a dash (-) in front of the path in the
Folder/File field. Exclusionary mappings apply to all access levels, even
though only one access level can be selected in the Access Level
field.
The following table describes the fields in the protections table.
|
Access Level |
The permission being granted. Each permission level includes all lower-level permissions, except for review.
For stream specifications, you can use P4 Admin to set stream spec access levels. For example, you can set an access level for a group or user, and then limit that access level to a subset of depots. Similarly, you can set an access level for a group and then remove it from a user in that group. The access levels for a stream spec are:
The denial levels for a stream spec in the P4 Admin built-in editor are:
You can also work with these access levels in P4 Admin as text, where:
Before you limit or remove an access level, make sure this access level has been provided. If you use
Suppose that, for the specified depot, you want to the user to have only
So, whereas granting an access level implicitly grants any implied access levels, denying an access level does not implicitly remove any other access level. All denials must be explicit. IMPORTANT: The 2020.1 release added protections modes that are specific to stream specs. By default, these permissions can exist in the protection table, but will not be used until the dm.protects.streamspec configurable has been set to |
||||||||||||
|
User/Group |
Indicates whether this line applies to a Perforce user or group. |
||||||||||||
|
Name |
A P4 Server user name or group name. You can use a wildcard. |
||||||||||||
|
The IP address of a client host. You can use a wildcard. |
|||||||||||||
|
Folder/File |
The part of the depot to which access is being granted or denied. To deny access to a depot path, preface the path with a dash (-). Exclusionary mappings apply to all access levels, regardless of the access level specified in the first field. |
||||||||||||
|
Comment |
Optional description of a table entry. Appends a comment at the end of a line using the ## symbols. For example: write user * 10.1.1.1 //depot/test/... ## robinson crusoe |
For details about how permissions work within P4 Server, see the Access authorization chapter of the P4 Server Administration Documentation.
When you look at the P4 Admin Permissions tab for any particular user, you will see the depots specified in the protection table. If that user has no access to a restricted depot, it will not expand to show any files. In this example, user1 can only see depot1:
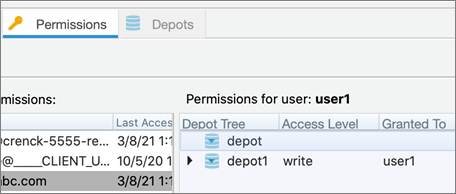
When user1 uses P4V, no depot will be visible except depot1.