Field security
Field security controls information users in security groups can view and change in items and workflow events. This security ensures users can only view information they need and helps protect any sensitive or confidential data.
Note: Security groups also have command security to limit the actions users can perform. See Command security.
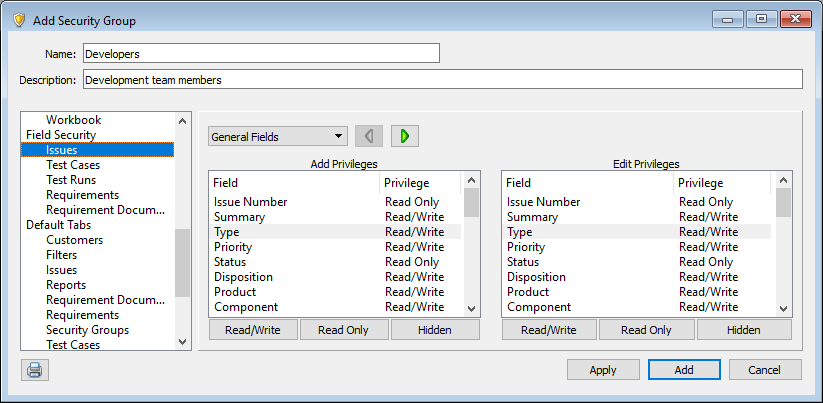
By default, users in new groups can view or edit every field. You can set the following security for each field to change the access.
- Read/Write access lets users enter and edit field values.
- Read Only access only lets users view field values.
- Hidden fields are not visible.
You can also set different field security for when users add and edit items. For example, you can set the Add privilege for the Type field to Read/Write and the Edit privilege to Read Only to let users set the field value when adding items and prevent them from changing the value when editing items.
Keep the following in mind when configuring field security.
- Field security does not apply to the following areas: SoloSubmit, XML import/export, and text file import/export. Any field in an email template can also be viewed by email recipients, but field security is enforced when users send email from Helix ALM.
- Users can be in multiple security groups. If any group a user is in gives permission to work with fields through field security, then the user has permission.
- System-generated and calculated custom field values are automatically set based on other field values or information in the project. For example, the Number, Status, Creation Method, and Date Last Modified fields have system-generated values. These values cannot be modified. You cannot set read/write access for these fields, but you can hide them.
- Linked item columns in list windows show the item Tag, Summary, and Status fields to all users regardless of licensing, if a field is hidden in their security group, or if their group can only work with items that pass a specific filter. You can hide linked items columns for groups if this information is sensitive. See Hiding fields.
Tip: As you work with security groups, you can use security group comparison reports to review permissions set for groups and compare settings between them. See Creating security group comparison reports.