The LDAP Integration runs as a P4 Plan SDK client process, which logs into the LDAP server to obtain user account information and also logs into the P4 Plan server to create and modify users. The schematic below depicts the hosts involved in an environment with LDAP integration and the network connections between them.
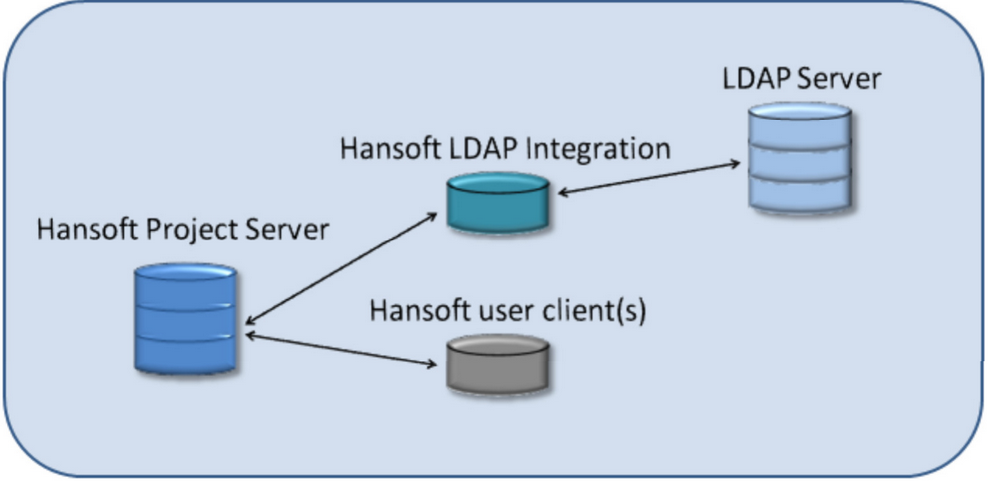
The four user accounts central to a properly configured LDAP integration are:
- An SDK account created in P4 Plan in order for the LDAP integration client to connect to the server.
- An LDAP user account that the LDAP integration uses to request information from the LDAP directory server. A dedicated service user account should be created in the LDAP directory before performing the LDAP integration. This account only requires read-only permissions to the LDAP directory.
- An e-mail server account on the SMTP server used by the LDAP integration to send notification e-mails.
- An administrative e-mail recipient account to which the LDAP integration addresses its notification e-mails. Correct configuration of this email address and the SMTP e-mail server network address is very important, as detailed diagnostic information is sent to it.
You will also need the network addresses (DNS or IP address) and port numbers of the P4 Plan server, LDAP directory server and SMTP e-mail server that the integration should connect to. In addition to the name of the server you will need the name of the server database whose resources the authentication integration will synchronize.
All diagnostic information is logged in the LDAP integration log files (in the \Log folder under the Integration's installation folder), facilitating functional verification and troubleshooting. The LDAP integration runs as a service that can be located on any server able to connect to both to the server and the LDAP directory server.
When logged in as "Administrator", you can manually enable and disable LDAP on individual accounts. You can also override the default binding of a resource to an LDAP account, by using the drop-down list in the LDAP tab in the users properties dialog.
You can also specify which login methods are enabled on a per-resource basis. For example, allowing users to log in with the credentials as well as with LDAP authentication provides a fallback in case the connection to the LDAP server breaks.
Users of other LDAP services can still use the P4 Plan LDAP Integration to create users in the P4 Plan database, but those users will have to use either the Helix Authentication Service or P4 Plan passwords for authentication.