Adding security groups
Security groups control access to the actions users can perform and the information they can work with. Users must be assigned to a security group before they can access a Helix ALM project.
Security groups have two levels of security you can set.
- Command security limits the actions users can perform. See Command security.
- Field security limits the information users can view and change in items and workflow events. See Field security.
You can configure multiple groups to provide the appropriate amount of security for different types of users based on their roles and responsibilities. Users can be in multiple security groups. If any group a user is in gives permission to perform an action through command security or work with fields through field security, then the user has permission.
1. Choose Create > Security Group. You can also click Add in the Security Groups list window.
The Add Security Group dialog box opens.
2. Enter a group Name and Description.
3. If you are adding the group to the project before adding users, skip to step 4 to set security options for the group.
If users or customers are available in the project, select the Users in Group category to add users to the group.
- To add a user or customer to the group, select them in the Available Users list and click Add.
- To search for users or customers, click Find User. See Searching for users and customers in fields.
- To limit the users and customers in the Available Users list, select any Display options.
- To remove a user from the group, select them in the Users in Group list and click Remove.
- To display the users in the group in user selection list fields, select Include users in pop-up menus or Include customers in pop-up menus. If the user is in multiple security groups and this option is selected for one or more of the groups, the user is displayed in user lists. Clear these options to limit users and customers displayed in user selection fields in items and workflow events, such as Entered by and Assign to.
Note: All users and customers in the project are displayed in the issue Found by/Reported by field even if the option to include them in pop-up menus is cleared for the group they are added to. For example, if a customer reports an issue, the customer is displayed in the Found by list in issues but not in other user selection fields, such as Entered by.
4. Set Command Security for each category.
Most commands are enabled by default. Clear any commands users in the group do not need access to. See Security commands for a list of available commands and descriptions.
- If you are setting security for issues, requirements, requirement documents, test cases, or test runs, select which items users in the group can work with. Select All <Items> to allow users to work with all items. Select No <Items> to prevent users from working with any items. Select <Items> passing filter and select a filter to allow users to only work with items that pass the selected filter. For example, if the View Issues command is enabled and the Must Fix filter is selected, users in the group can only view issues that pass the Must Fix filter. If a user is in multiple groups, they can work with items that pass any of the filters selected in the groups. You can also select an option to only allow users to work with issues they reported or items they created. If a user is in multiple groups, the items the user can work with are only restricted if the option is selected in all groups they are in.
- By default, security for requirements is the same for all requirement types. You can override the default setting and set different security for each type. Select a type from the list, clear Use values from <All Requirement Types>, and set the command security for the type. An asterisk indicates the types that do not use the default settings. Security for requirement events applies to all types.
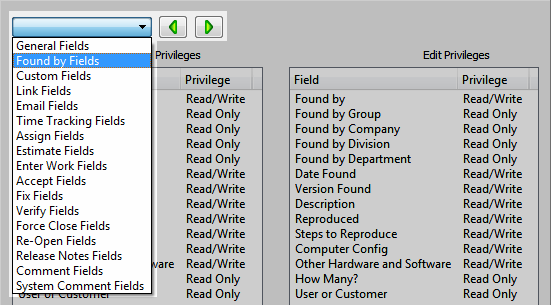
5. Set Field Security for each category.
To change access to a field, select it and click Read/Write, Read Only, or Hidden. Read/write access lets users enter and edit field data. Read-only access only lets users view field data. Hidden fields are not visible. You can set different field security for when users add and edit items.
- By default, users in new groups can view or edit every field. Select a field category from the list to view fields or click
 and
and  to move between categories. Make sure to set Add and Edit privileges for all field categories.
to move between categories. Make sure to set Add and Edit privileges for all field categories.
- By default, security for requirements is the same for all requirement types. You can override the default setting and set different security for each type. Select a type from the list, clear Use values from <All Requirement Types>, and set field security for the type. An asterisk indicates types that do not use the default settings. Security for requirement events applies to all types.
6. Select the Notes category and enter any information about the group, such as why it was created or the type of users in it.
Note: You will use the Default Tabs and Default Views categories when editing security groups. See Changing default list window tabs and requirement document views for security groups.
7. Click Add.
The security group is added.
Note: You can assign new users to a group when adding them to the project. See Managing user and customer contact information and passwords. You can also edit the group to add multiple new users at the same time. See Editing security groups.